Computerware Blog
You’ve probably seen the word “metaverse” pop up in your news feed at least once or twice over the past couple of months, but the concept can be a bit difficult to understand, as it’s a bit complicated by nature. Let’s discuss what the metaverse is, why it’s important today, and what you might expect from a metaverse in the future.
Using email to trick users is something that hackers have done for ages, but they usually find themselves tucked away in the spam folder where they belong, or blocked entirely by enterprise-level content filters. Hackers, however, are a crafty lot, and they have discovered ways to break through these measures through the use of a surprising third party: social media websites.
Facebook is by far the largest social media network and it does bring a lot of value to a lot of people. Whether that be for personal use or professional use, Facebook has staked a claim as the most successful technology company in the world. With this comes scrutiny, especially if you’ve operated the way Facebook has over the past few years. Let’s take a look at a situation that Facebook is dealing with in 2021.
Facebook is a great tool to connect with people in both your personal and professional life, but having a business page on Facebook can attract a lot of attention--and it’s not necessarily wanted in certain cases. For example, what if someone started slinging expletives at your page without your consent? This doesn’t just hurt your feelings; it makes you look bad. This week’s tip is dedicated to blocking unwanted content on your Facebook page.
As a technology, social media has been a revelation for individuals and businesses, alike. From a technology management perspective, it also has produced a lot of wasted man-hours over that time. Today, we will look at the pros and cons of social media for the small and medium-sized business, and how to get so the use of it is a net-positive position for your company.
Facebook has had a lot of pressure on it over the past few years. After taking the company public in 2012, the world’s most popular social network went on to make several high-profile acquisitions (Oculus, Instagram, etc.) to solidify their position in the market. As a result the company has a lot of responsibility to protect the immense amount of data that it takes in. This has opened up the tech giant to be heavily maligned in the media over the past year.
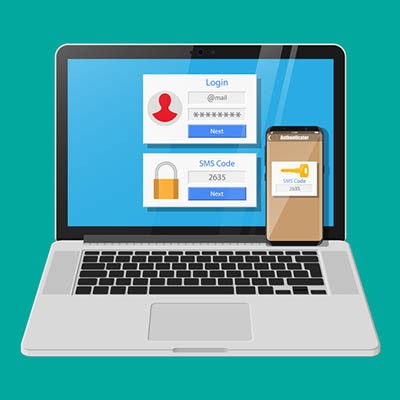
If you’re like its over 2.19 billion other active users, Facebook has quite a bit of your personal information stored in it, and the risks that this implies only grow if your business is also represented on the social network. If your account isn’t protected as much as it could be, you could find yourself at risk of identity theft or other crimes. This is why we recommend activating two-factor authentication on Facebook.
In the modern business setting, collaboration drives productivity. As a result, many software developers are producing software with collaboration in mind. Since these developers are all in competition with each other for market share, they are typically trying to build on more advanced features to outmaneuver the other companies. Some of the biggest names in the industry have recently updated their products to make collaboration a priority. This week we’ll take a look at updates made to Facebook Workplace, Gmail, and Slack.
The Internet is prone to change. We all know this and have experienced it firsthand. Even though we may understand this reality, it can still be rather shocking when we’re confronted with it. The latest statistics show us how the current changes of the Internet have huge implications about how we’ll all interact with the web moving forward, which may spell doom for doing “online business as usual.”
Back in 2011, Facebook released their Messenger app. It was designed to be a chat system that could be used to communicate outside of the Facebook app. Since then, Facebook has provided Messenger with much more functionality than your average everyday messaging system. In fact, Messenger might now offer features that could be helpful for your business.
It’s a typical work day. You’re going about your business, when you decide to take a short break and check Facebook. Maybe you see a post that you’d like to share, but you’d rather not have that post on your timeline. While you could just delete it later, there’s a new feature that lets you share a post to your news feed, without posting it on your timeline.
What makes Facebook so valuable is that it connects you to a wide variety of people. However, for many users, having such a diverse audience means holding back on sharing their personal opinions, which kind of takes the fun out of social networking. Did you know that Facebook allows you to exclude certain people from seeing your posts? For this week’s tip, we’ll show you how to take advantage of this feature.
 Employees who are addicted to social media is a problem for modern businesses. Despite the professional networking benefits of social media, it can be a major distraction and time-waster. Before you lock down all social media websites on your network, you should first try to understand why humans have such a hard time leaving social media alone.
Employees who are addicted to social media is a problem for modern businesses. Despite the professional networking benefits of social media, it can be a major distraction and time-waster. Before you lock down all social media websites on your network, you should first try to understand why humans have such a hard time leaving social media alone.
 It’s a known fact that social media is a great asset for the modern business owner to leverage, but you wouldn’t believe how often it’s misconstrued as a waste of time. In fact, social media outlets like Facebook, Twitter, LinkedIn, and even YouTube, are so commonplace nowadays in the business world that your organization could fall behind others that properly utilize them. Facebook, in particular, is a powerful tool that can be used for online networking purposes.
It’s a known fact that social media is a great asset for the modern business owner to leverage, but you wouldn’t believe how often it’s misconstrued as a waste of time. In fact, social media outlets like Facebook, Twitter, LinkedIn, and even YouTube, are so commonplace nowadays in the business world that your organization could fall behind others that properly utilize them. Facebook, in particular, is a powerful tool that can be used for online networking purposes.
 Facebook has become the most popular social media outlet in the world, but in the eyes of corporate offices, it can be an immense time waster and productivity killer. However, it can be an incredibly efficient tool for connecting with other professionals, sort of like a pseudo-LinkedIn. To counter this stigma associated with social media in the workplace, Facebook has produced Facebook at Work.
Facebook has become the most popular social media outlet in the world, but in the eyes of corporate offices, it can be an immense time waster and productivity killer. However, it can be an incredibly efficient tool for connecting with other professionals, sort of like a pseudo-LinkedIn. To counter this stigma associated with social media in the workplace, Facebook has produced Facebook at Work.
 It's a trap! As more people subscribe to social media networking sites, we can expect more scammers to weasel their way into our friend bases. Especially when using Facebook, you'll need to be on the look out for scammers. Here are some warning signs of fake Facebook friends to consider in order to keep your profile safe.
It's a trap! As more people subscribe to social media networking sites, we can expect more scammers to weasel their way into our friend bases. Especially when using Facebook, you'll need to be on the look out for scammers. Here are some warning signs of fake Facebook friends to consider in order to keep your profile safe.
 In 2012, Facebook hit one billion active users. Facebook is the undisputed king of social media, but this does not mean that their subjects are happy. In a January 2013 study, online news site 24/7 Wall St. found Facebook to be one of America's top ten most hated companies. This study factors in customer and employee satisfaction, as well as stock performance.
In 2012, Facebook hit one billion active users. Facebook is the undisputed king of social media, but this does not mean that their subjects are happy. In a January 2013 study, online news site 24/7 Wall St. found Facebook to be one of America's top ten most hated companies. This study factors in customer and employee satisfaction, as well as stock performance.